IAM enumeration
Objective: Using the access credentials, enumerate users, roles, and policies on the AWS account
Console Based Enumeration
Click on the lab link button to get access to the AWS lab credentials.
Sign-in into the AWS console.
Search for the IAM dashboard and navigate to it.
Click on Users.
To enumerate a user click on the username. Check user Permissions and policies.
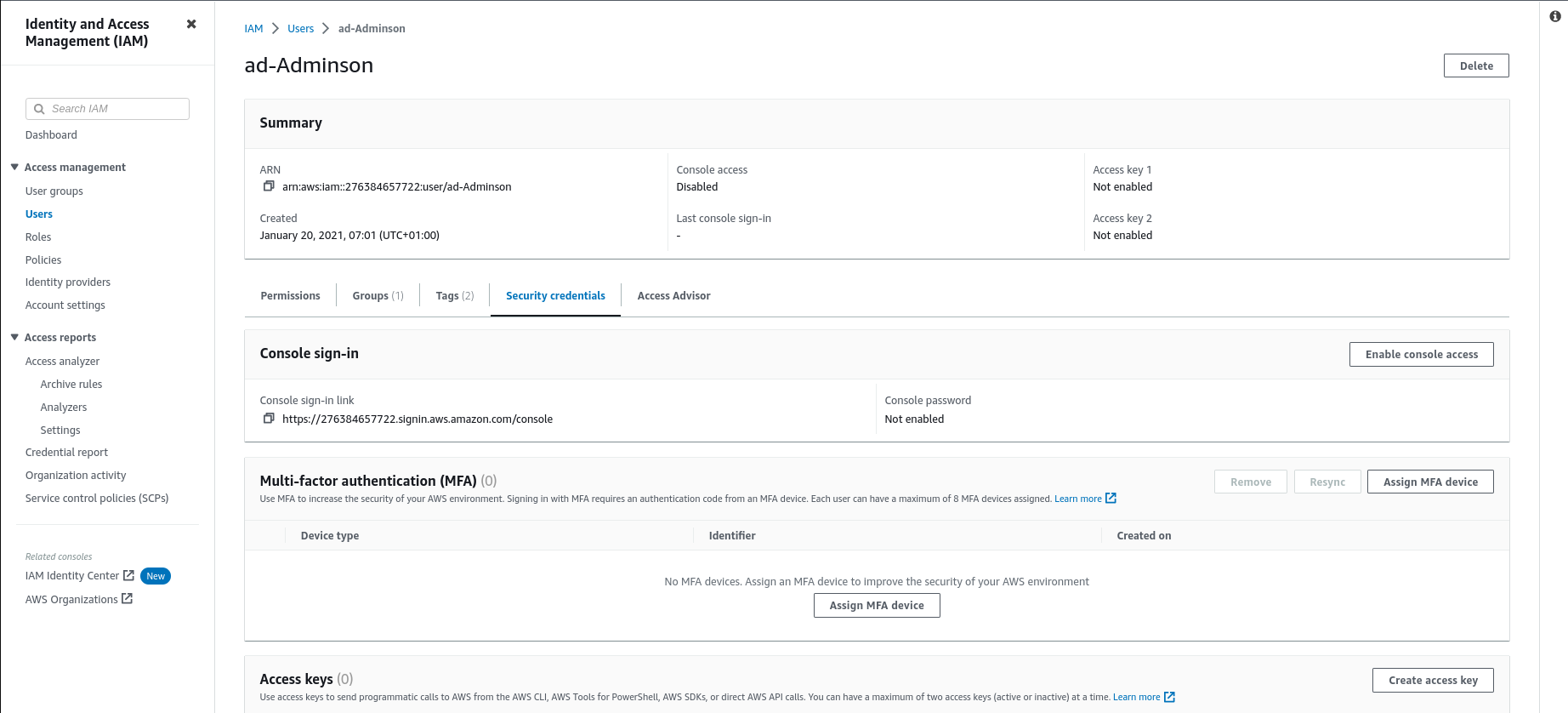
Check Groups for the user.
Check the user’s Security credentials.
Similarly check for other user’s permissions.
Check Groups and Security credentials for the user.
Check the user’s access keys and ssh keys.
Click on Groups on the left panel to enumerate groups.
Click on the group name to open group details. Check for the users that are part of the group.
Check the for the group attached policies.
Similarly check for the other groups.
Click on Policies in the left pane to enumerate policies.
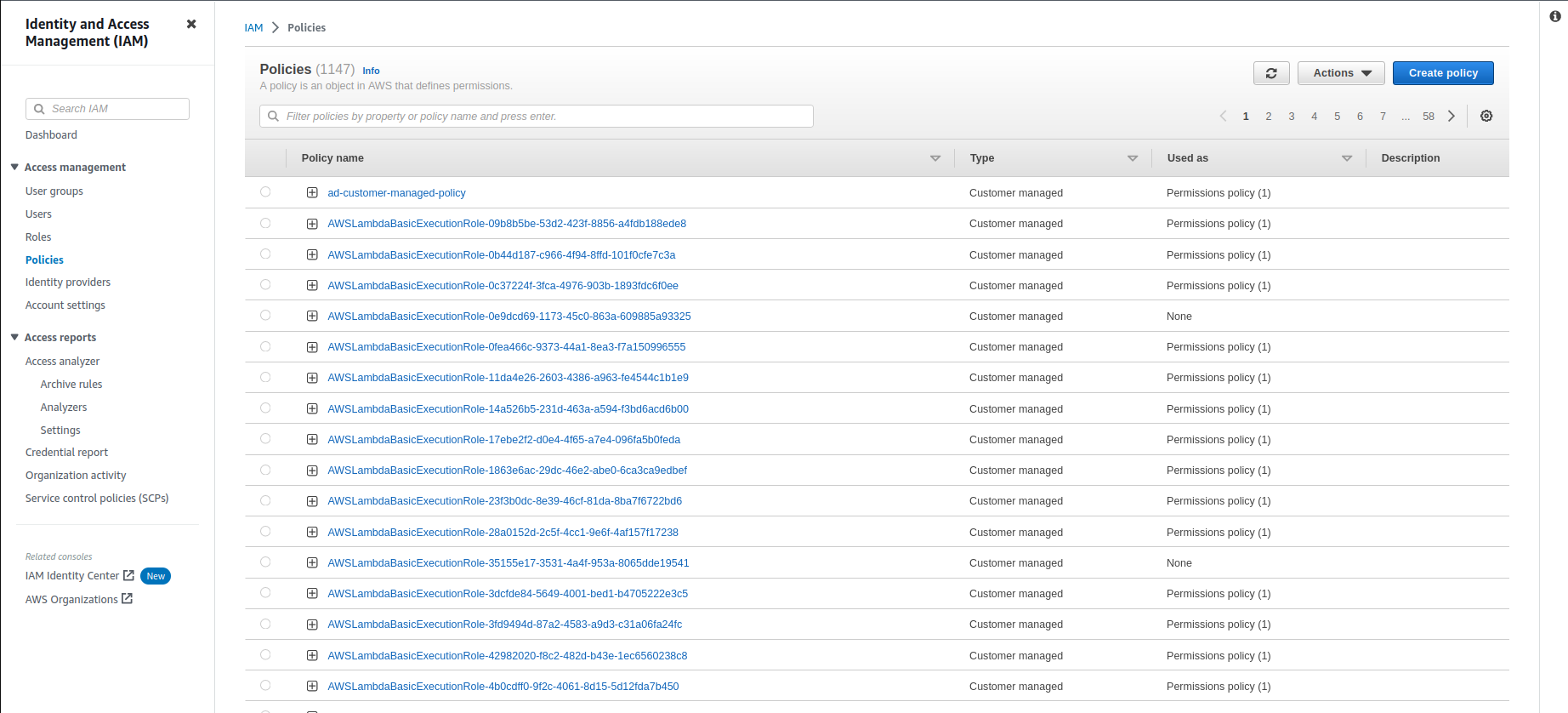
Check Customer-managed and AWS managed policies.
Click on the policy name to enumerate the policy.
Check policy document, policy usages and policy permissions.
Similarly enumerate other AWS managed policies.
Click on Roles on the left panel to enumerate roles.
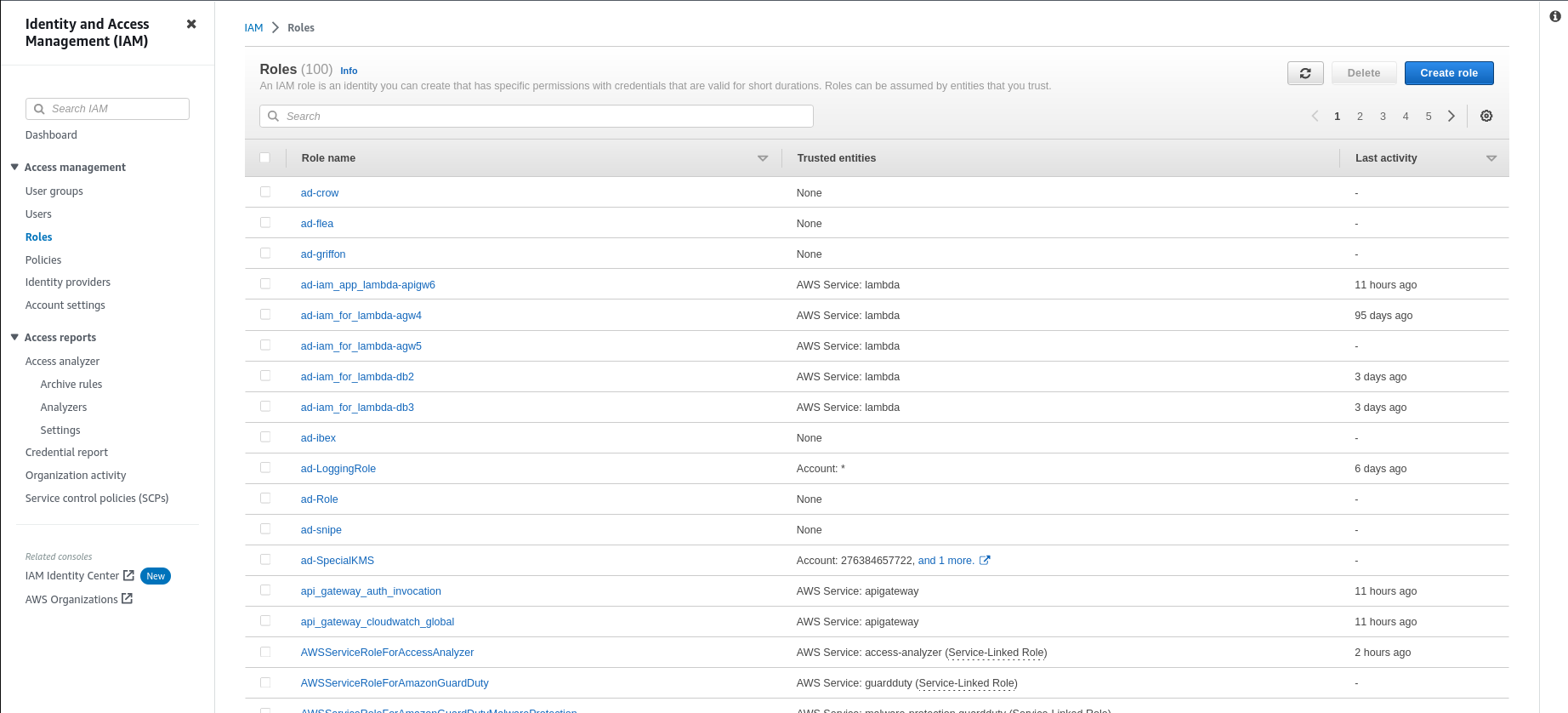
Click on role name to enumerate roles for the AWS account.
Check the role trust policy.
Check role’s Trusted entities.
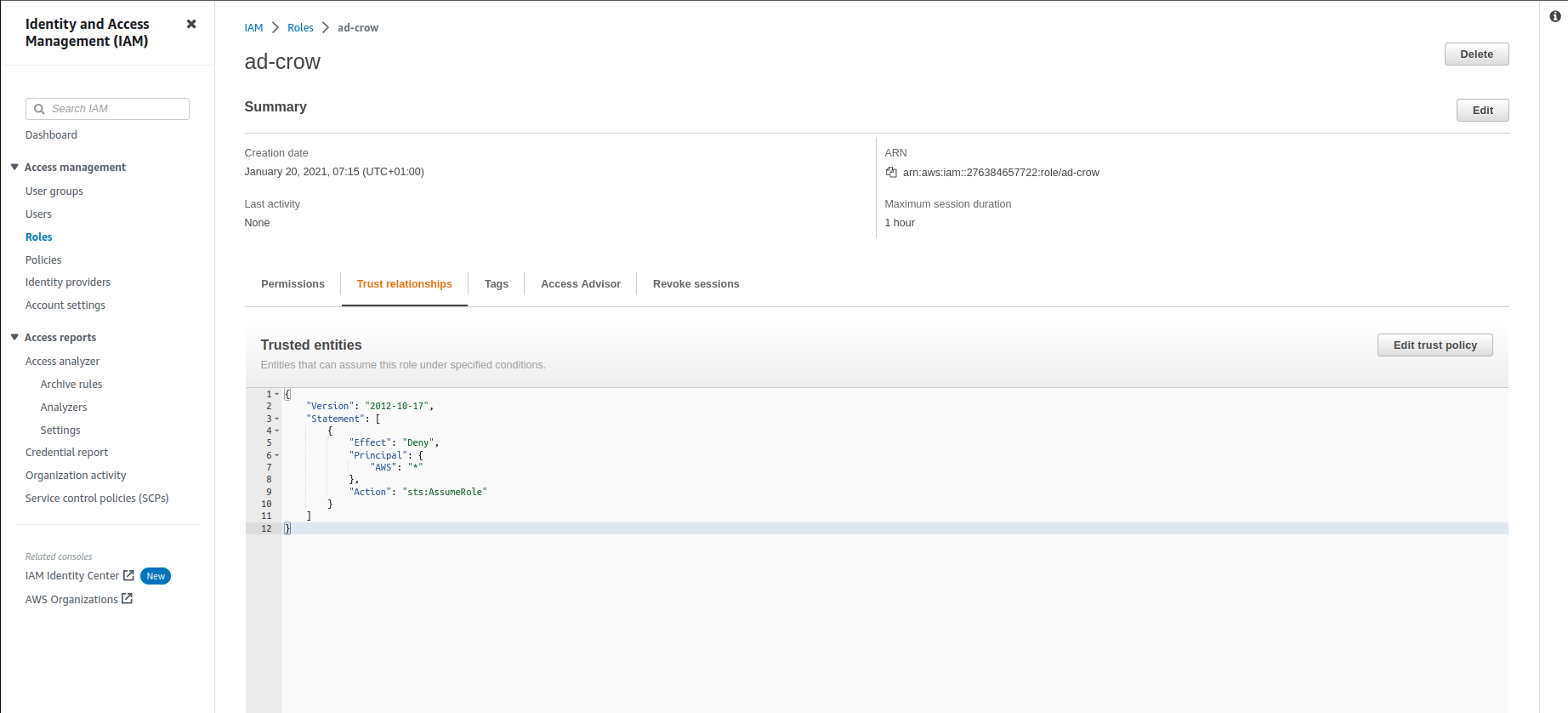
Check the role’s inline policies.
Check the role’s Trusted entities.
Similarly enumerate other roles.
CLI Based Enumeration
Click on the lab link button to get access to the AWS lab credentials.
Configure AWS CLI to use the provided credentials.
aws configure
Get a list of the users on the AWS account. Briefly check UserName, UserId and Arns.
aws iam list-users
Check groups for users.
aws iam list-groups-for-user --user-name ad-adminson
Check policies attached to the user.
aws iam list-attached-user-policies --user-name ad-user
Check for any signing certificates for the user.
aws iam list-signing-certificates --user-name ad-user
Check for any public ssh keys for the user.
aws iam list-ssh-public-keys --user-name ad-user
Get ssh key details.
aws iam get-ssh-public-key --user-name ad-user --encoding PEM --ssh-public-key-id APKAUAWOPGE5M47NZEIT
Check for MFA devices for users.
aws iam list-virtual-mfa-devices
Check for user login profile.
aws iam get-login-profile --user-name ad-user
Enumerate groups for the AWS account.
aws iam list-groups
Check which policies are attached to the group to enumerate permissions.
aws iam list-group-policies --group-name ad-admin
aws iam list-attached-group-policies --group-name ad-admin
Enumerate policies for the AWS account. Without any filter the command will return all the IAM managed policies (AWS Managed Policy + Customer Managed Policies).
aws iam list-policies
Without any filter the command will return all the IAM managed policies (AWS Managed Policy + Customer Managed Policies)
Search for customer managed policies.
aws iam list-policies --scope Local | grep -A2 PolicyName
The command aws iam list-policies –scope Local will return the customer managed policies. grep -A2 PolicyName> is used to search for the PolicyName string and the next two lines after the string match.
Check for policy details of ad-customer-managed-policy.
aws iam get-policy --policy-arn arn:aws:iam::276384657722:policy/ad-customer-managed-policy
Get the policy version document to check permissions that the policy grants.
aws iam get-policy-version --policy-arn arn:aws:iam::276384657722:policy/ad-customer-managed-policy --version-id v1
Enumerate roles on the AWS account.
aws iam list-roles
Check details for roles.
aws iam get-role --role-name ad-loggingrole
This role can be assumed by any AWS resource.
Check for policies attached to roles.
aws iam list-attached-role-policies --role-name ad-loggingrole
aws iam list-role-policies --role-name ad-loggingrole